By Anju Chopra, SVP Technology, Identity Theft and Breach Notification, and Keith Wojcieszek, Associate Managing Director, Cyber Risk
Many of the high-profile cybersecurity breaches of the last several years share a common, disturbing thread: The breach was not the result of a direct attack on the targeted organization, but instead due to exposures arising from vendors and other trusted third parties. These secondary vulnerabilities allowed bad actors either direct access to the target company’s systems or to sensitive company information that had been entrusted to the vendor.
Unfortunately, the potential security problems raised by interwoven IT systems of vendors, partners, customers and others will only grow more acute. The integration of data across supply chains is a key component of both the digital transformation that is reconfiguring companies in diverse sectors from chemicals to consumer goods, and of emerging technologies such as the Internet of Things. Furthermore, in addition to increased connectivity between organizations, there is also more connectivity between organizations and individuals, as the boundaries between work and home—and work networks and home networks—continues to erode in today’s “always on” business environment. The result is a massive, growing and porous hyper-network that offers abundant opportunities for sensitive data to be lost, exposed or stolen.
A Spotlight on Third-Party Cyber Risk
The need to monitor the cybersecurity of third parties has put a spotlight on cyber supply chain risk management (C-SCRM). The baseline C-SCRM approach is for companies to require vendors and others to fill out a questionnaire and the review of SOC reports, ISO certifications and similar documents. This information provides a good foundation for vendor assessment. However, it doesn’t measure the state of a company’s cybersecurity so much as the company’s cybersecurity culture. A company that can check these boxes has clearly made the investment in the people and resources necessary for a credible cybersecurity function. But as important as this is, it sheds little light on actual vulnerabilities that may exist.
This is why some companies take an extra step in the due diligence process and have vulnerability scans and penetration tests conducted on vendor systems. This provides a much more tangible assessment of how a vendor system performs under real-world conditions. But scans and tests have their own limitations. They give you a snapshot of the security of the vendor system at that moment, but they don’t say anything about the data held by the vendor that may have made its way outside the vendor’s firewall, whether due to malware or, say, an employee working remotely and using an unsecured Wi-Fi network.
The Role of Dark Web Monitoring
Forward-thinking organizations are responding by incorporating dark web monitoring as the third prong of their cyber supply chain risk management program (see Figure 1). Dark web monitoring scours unindexed sites, chat rooms and P2P networks that are often hidden behind an anonymizing browser such as Tor and often require special credentials to access. Not surprisingly, the dark web is a hotbed of illicit activity, including the buying and selling of illegal drugs, counterfeit goods and stolen data such as customer credit card and account data, employee data and proprietary corporate information that can range from contracts to sensitive boardroom documents.
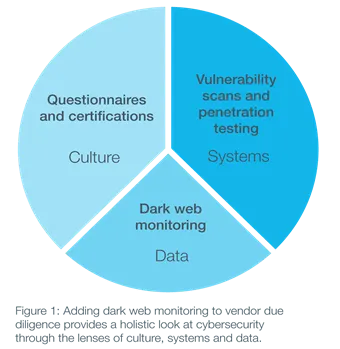
Continuous monitoring of the dark web for client provided data that may have originated from vendor systems and of chat-room discussions regarding the vendor adds important insight during both the vendor due diligence process and the working relationship:
- It paints a fuller picture of a vendor’s system security that augments security surveys and testing.
- Because there is often a considerable time lag between the occurrence of a breach and its discovery, dark web monitoring can provide an invaluable early warning mechanism for breaches of vendor networks.
- It helps you develop insight into the extent to which the vendor and its systems are a subject of interest among bad actors and thus of potential future attacks.
Consider the experience of a flag carrier airline that had asked us to monitor its own presence on the dark web. While doing so, we discovered that a sizable batch of the airline’s customer itineraries had been exposed—not due to a breach of its own network but rather a breach of a travel agency network. Critically, the travel agency was unaware that the breach had occurred.
Fortunately, the breach was discovered, allowing the airline to inform the affected passengers and take other remedial action. Had the airline been conducting dark web monitoring of the information it provided to this and other travel agencies as part of its regular cybersecurity program, it may well have detected this exposure, and other similar vendor network vulnerabilities, even earlier. As an additional method of protection, organizations can monitor key terms, IP addresses, and domains provided by their vendors in order to reduce their own risk by better understanding the potential exposures of their third parties.
Extracting Signal From Noise
Comprehensive dark web monitoring platforms combine intelligence gleaned in three ways (see Figure 2). First, data collection scripts use IP addresses, email addresses, keywords and other information provided by the company to identify data that may have originated with the vendor that is now on the dark web. Artificial intelligence programs then analyze that data to extract signal from noise through disambiguation, contextual analysis and other tools.
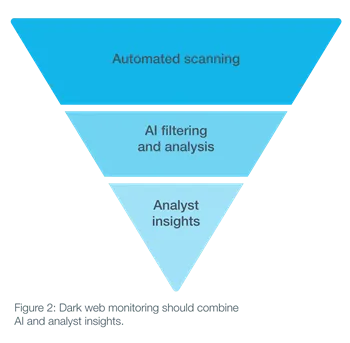
The intelligence gathered through these automated methods is then reviewed and further refined by a human analyst, who can add additional information potentially gleaned from conversations in private chat rooms where data may be exchanged for criminal purposes. Being privy to real-time online exchanges between bad actors can provide additional insight on emerging threats and attack vectors. This monitoring can yield actionable intelligence which can then be used to prioritize and design effective responses. The result is another element to help create the continuous, real-time picture of potential illicit data exposure, that goes far beyond the stolen emails and passwords that may capture headlines, but which do not reflect all the larger strategic risks that come from other types of exposed corporate or customer information.
Because supply chain cyber risk is based on the scope of the vendor-customer data exchange relationship and not necessarily on the size of the vendor, dark web monitoring—which is unobtrusive from the vendor’s perspective and scales easily—should be part of a company’s due diligence process for all vendors, large or small. And because dark web monitoring can be implemented quickly, it can be used as a more immediate source of security insight while security assessments and penetration testing are underway.
As the global connectivity between organizations continues to accelerate, cybersecurity due diligence regarding vendors and other partners will become even more critical to a company’s overall cyber strategy. Adding dark web monitoring to that process provides a holistic view of the culture, systems and data of those third parties—and the potential for early and actionable intelligence regarding cyber threats that might otherwise go undetected.


